How to crack the World Circular Day OKX Private Key Puzzle Prize (full code included)
Author: Inventors quantified, Created: 2023-03-14 23:25:45, Updated: 2024-11-29 18:57:29
Look at the neighboring temple group saying OKX is doing a World Circular Day unraveling event, the topic is as follows:

I'm a senior gardener, and when I saw the news, my mouth was slightly raised, and I opened my MacBook Pro, and I didn't say a word, and I started.
The analysis
The official said that there are 61 keys in the image that overlap with the circularity, the private key is 32 bytes in length, which is converted to hex, which is 64 bits plus the 0x prefix, a total of 66 bits, there are already 61 bits, the first row of 0X in the diagram is obviously not circularity, the private key starts in the front, then there are 5 to the right ((0123456789ABCDEF) the random arrangement of these characters, the violence runs smoothly, the hand starts.
Use the Mac's built-in tool to easily customize the color

This is what it looks like, and then the Mac automatically recognizes the characters in the image, and we copy directly:
3.141592653589793230X1D64338
А694502884197169399375105820
974925E123078164062862089986
28033DB034211706409914808651
32823066470ED424609550582231
8B3
81284
•探索,
038
永无止境
027
493
05%
0128
4756482337867831731712019091
47D9E56692346034861045432664
8213393607743749141273724587
006606315588174881BEEA209628
2925409192744436789259036001
This is definitely not working, we manually modified it, and the unconfirmed ones that were hidden in the image were marked with a *, not sure, we'll talk more about that later.
The rest is stuck in the diagram, which can be judged by looking at the font's other font shape, and this time we're in Python, calculating the difference between the two, the same one with
img = '''
3.141592653589793230X1D64338
A694502884197169399375105820
974925E123078164062862089986
28033DB034211706409914808651
32823066470ED424609550582231
8B32594081284811174502841027
0193**2*D2299964462294895493
0381960EFC8103F9365933446128
4756482337867831731712019091
47D9E56692346034861045432664
82133936077A3749141273724587
006606315588174881BEEA209628
2925409192744436789259036001
'''
# 真实圆周率
real='''
3.14159265358979323846264338
3279502884197169399375105820
9749445923078164062862089986
2803482534211706798214808651
3282306647093844609550582231
7253594081284811174502841027
0193852110555964462294895493
0381964428810975665933446128
4756482337867831652712019091
4564856692346034861045432664
8213393607260249141273724587
0066063155881748815209209628
2925409171536436789259036001
'''
items = img.strip().split('\n')
diffStr = ''
for pos, line in enumerate(real.strip().split('\n')):
for i, c in enumerate(line):
imgLine = list(items[pos])
if line[i] == imgLine[i]:
imgLine[i] = '_'
else:
diffStr += imgLine[i]
items[pos] = ''.join(imgLine)
print('\n'.join(items))
print(diffStr, 'Len:', len(diffStr))
The results are as follows:
___________________0X1D_____
A694________________________
____25E1____________________
____3DB0________4099________
___________ED42_____________
8B32________________________
____**_*D2299_______________
______0EFC___3F93___________
________________731_________
_7D9E_______________________
__________7A37______________
__________________BEEA______
________92744_______________
0X1DA69425E13DB04099ED428B32***D22990EFC3F937317D9E7A37BEEA92744 Len: 64
So if you add three more digits, and there's three uncertains in there, you can try to remove him, because if you exclude the other 61 digits, it's okay. Leave only the most definite differences, and finally consider the following prefix:
0X1DA69425E13DB04099ED428B32D22990EFC3F937317D9E7A37BEEA92744
You can also go down to Python, and then you can go down to the OK chain, and you can compare which private key has the balance, and you can also choose the public key that has 314 USDT transferred, so it's faster, and you can look at the website and see if there's any gas left, and then you can look directly at the balance.
import sys
import web3,time,logging
from eth_account import Account
from web3 import Web3
logging.basicConfig(level=logging.INFO, format='%(asctime)s %(message)s')
w3 = Web3(Web3.HTTPProvider("https://exchainrpc.okex.org"))
logging.info(w3.clientVersion)
found = None
def get_balance_gas(key):
global found
_counter += 1
address = Account.from_key(key).address
logging.info('fetch address %s %s' % (found, address))
while True:
try:
balance = w3.eth.get_balance(address)
break
except:
logging.warning(traceback.format_exc())
time.sleep(1)
continue
if balance != 0:
found = key
raise BaseException('Found balance: %s %s' % (address, balance))
return balance
from concurrent.futures import ThreadPoolExecutor
executor = ThreadPoolExecutor(max_workers=50)
keys = []
prefix = '1DA69425E13DB04099ED428B32D22990EFC3F937317D9E7A37BEEA92744'
# 无所谓优化算法了, 争分夺秒跑密钥
ch = '0123456789ABCDEF'
for a in range(0, 16):
for b in range(0, 16):
for c in range(0, 16):
for d in range(0, 16):
for e in range(0, 16):
keys.append("0x"+prefix+ch[a]+ch[b]+ch[c]+ch[d]+ch[e])
print('all keys:', len(keys))
tasks = [None for t in keys]
for idx, key in enumerate(keys):
tasks[idx] = executor.submit(get_balance_gas, key)
for t in tasks:
t.result()
You can see that it takes 10,485,76 rounds to run on a server that I have, and it's much faster with multiple threads.
2023-03-15 00:20:19,491 exchain-v1.6.8.5
all keys: 1048576
2023-03-15 00:20:20,372 fetch address None 0xc20C41f06F2428a0FD84ef03Ec6960992F5f8016
2023-03-15 00:20:20,473 fetch address None 0xcFa87ee54bc1c14c09a3AB3f41640bBab5C5480a
2023-03-15 00:20:20,483 fetch address None 0x126E922652f8B276F231D0eCA94d98685a26a45D
以下省略......
In the anxious wait, bad news came, the tactics didn't work out before the exit, all shown None
The summit turns
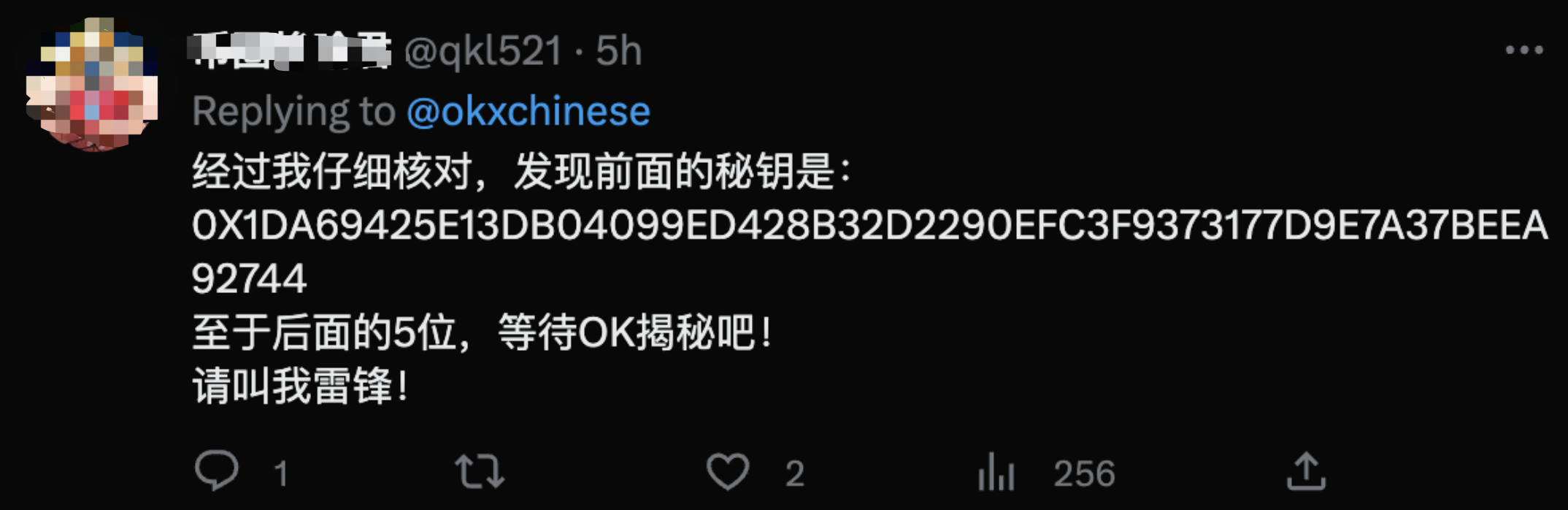
I started to look at the discussion on Twitter and found out that everyone was taking the same steps I was taking, but strangely, no one had said anything about decryption being successful, and the official list of the top 61 was not published, so a strange reply caught my attention because there was a difference between the two.D2299I'm sure there's no ambiguity, but he also seems confident.

But this guy posted 61 digits and it's D2290, and he said it was checked out carefully, no matter what, just by luck, it's a waste of electricity anyway.
With a spirit of experimentation, I found 61 of the other people who commented that they found, and they all looked confident.
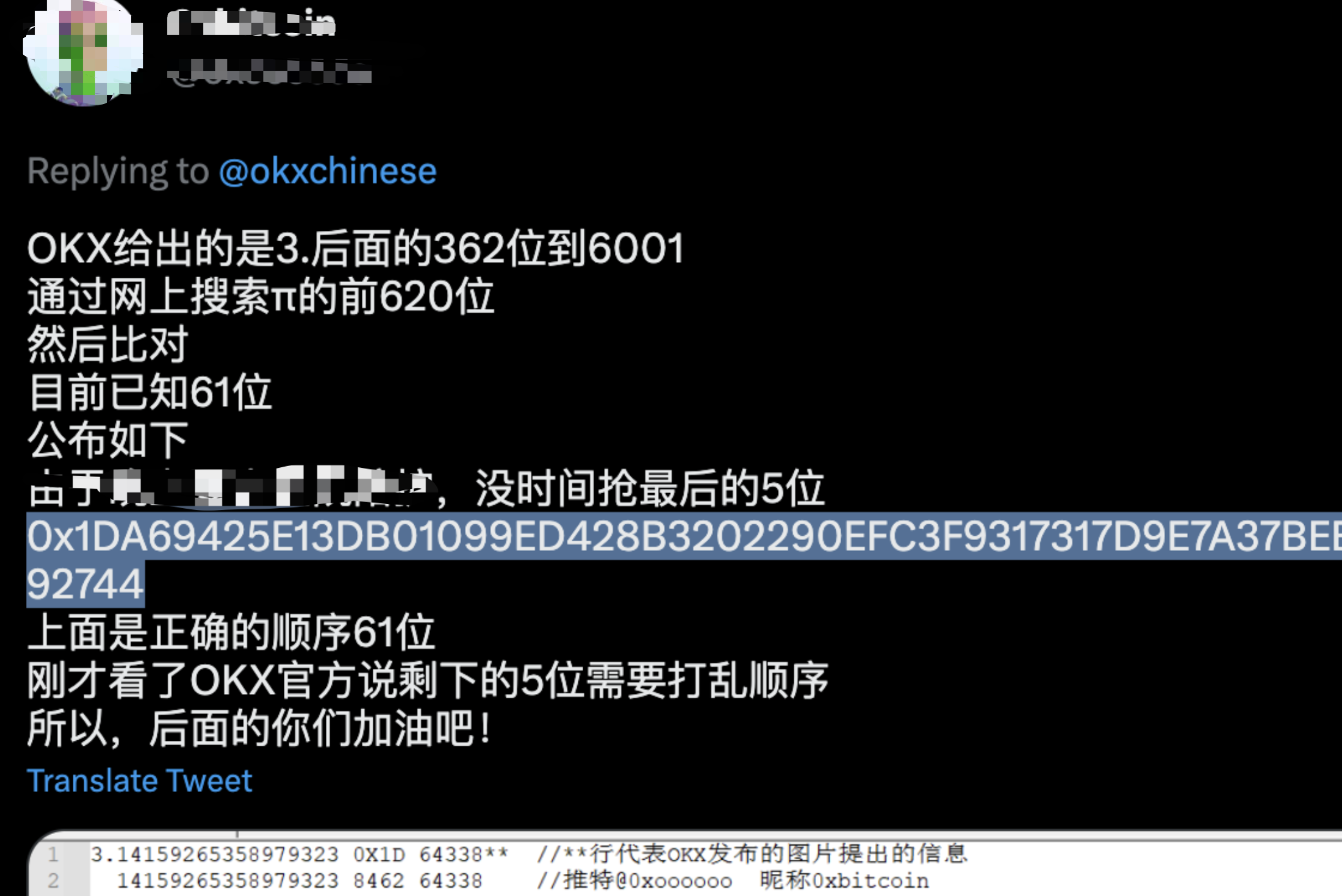
All the prefixes found in the comments section are collected and then scrolled through with the same code, with the basic code unchanged, unreplicated.
prefixs =[
'1DA69425E13DB04099ED428B3202290EFC3F9317317D9E7A37BEEA92744',
'1DA69425E13DB04099ED428B32D2290EFC3F9373177D9E7A37BEEA92744',
'1DA69425E13DB04099ED428B320D2290EFC3F937317D9E7A37BEEA92744',
'1DA694255E3DB040990ED428B3208890EFC3F937317D9E7A37BEEA92744',
'1DA69425E13DB04099ED428B3202299EFC3F9317317D9E7A37BEEA92744',
'1DA69425E13DB01099ED428B3202290EFC3F9317317D9E7A37BEEA92744',
'1DA69425E13DB04099ED428B32D2290EFC3F9317317D9E7A37BEEA92744',
'1DA69425E13DB04099ED428B32D22990EFC3F937317D9E7A37BEEA92744',
]
In fact, there's more new posts on the back, and one of the brothers has a different PI than mine, which is amazing. I'm going to run with these first, and I can't believe my eyes, but I ran out and showed that one of the keys in front of me is correct, which is not scientific, the private key is:
1DA69425E13DB04099ED428B32D2290EFC3F9373177D9E7A37BEEA92744C8155
He's D229 here, but the picture is clearly D2299, and 731 has a 7 behind it, and he's two, and he's a 7 behind 731. But it's exactly 61 digits, it's unknown how he calculated it himself, it's very curious, but I don't have any doubts about my own operation, look in the comment section and say that the official customer is convinced that there is another version of the round rate, I'm lonely, with the knowledge that I've learned and the current understanding of the universe, the round rate this irrational number can represent the infinity of the universe, its fraction never repeats or ends, you can understand him as the UUID of your universe, if there are other versions, maybe from the parallel world.
This is another big brother's response to customer service after being questioned:
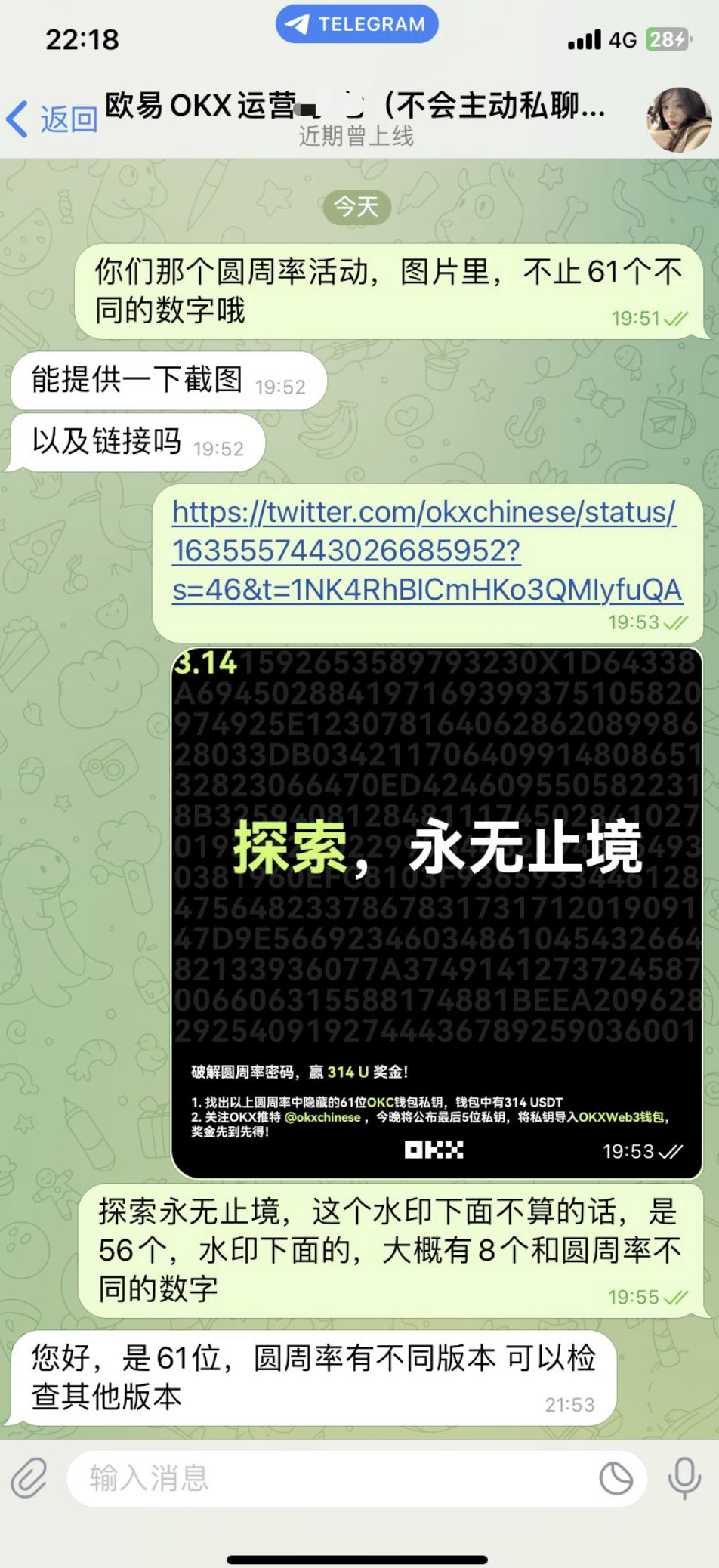
It's a bit of a learning curve.
Web3 currency conversion code
And finally, the code to transfer the bonus, this time directly to the Web3 function of the FMZ platform, where the chain address is set to OKC and works, and the private key is added to the exchange and it doesn't work anyway, and then both lines are done, executed directly in the debug mode.
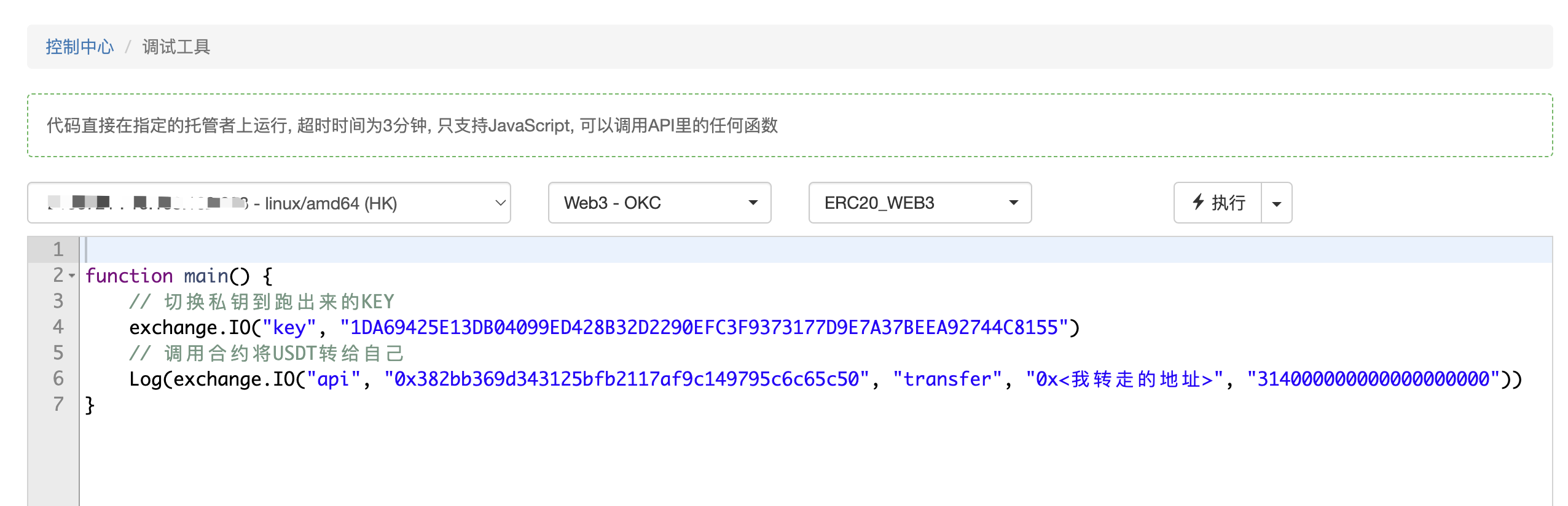
The proof
The address of the public key that was hacked
>>> from eth_account import Account
>>> Account.from_key('0x1DA69425E13DB04099ED428B32D2290EFC3F9373177D9E7A37BEEA92744C8155').address
'0x0bd08825e05e540C9508961a32E58D14da47275A'
See the link:https://www.okx.com/cn/explorer/okc/address/0x0bd08825e05e540c9508961a32e58d14da47275a
TX: I'm not going to be able to do this.https://www.okx.com/cn/explorer/okc/tx/0x4211418b09571011417257201aaf10fc3c5d638809a9456eb5aba5fe8c5d4e2c
You can see that the recipient address is
0x25f0a126be95f437ee71d7c4de725567c5f6c731
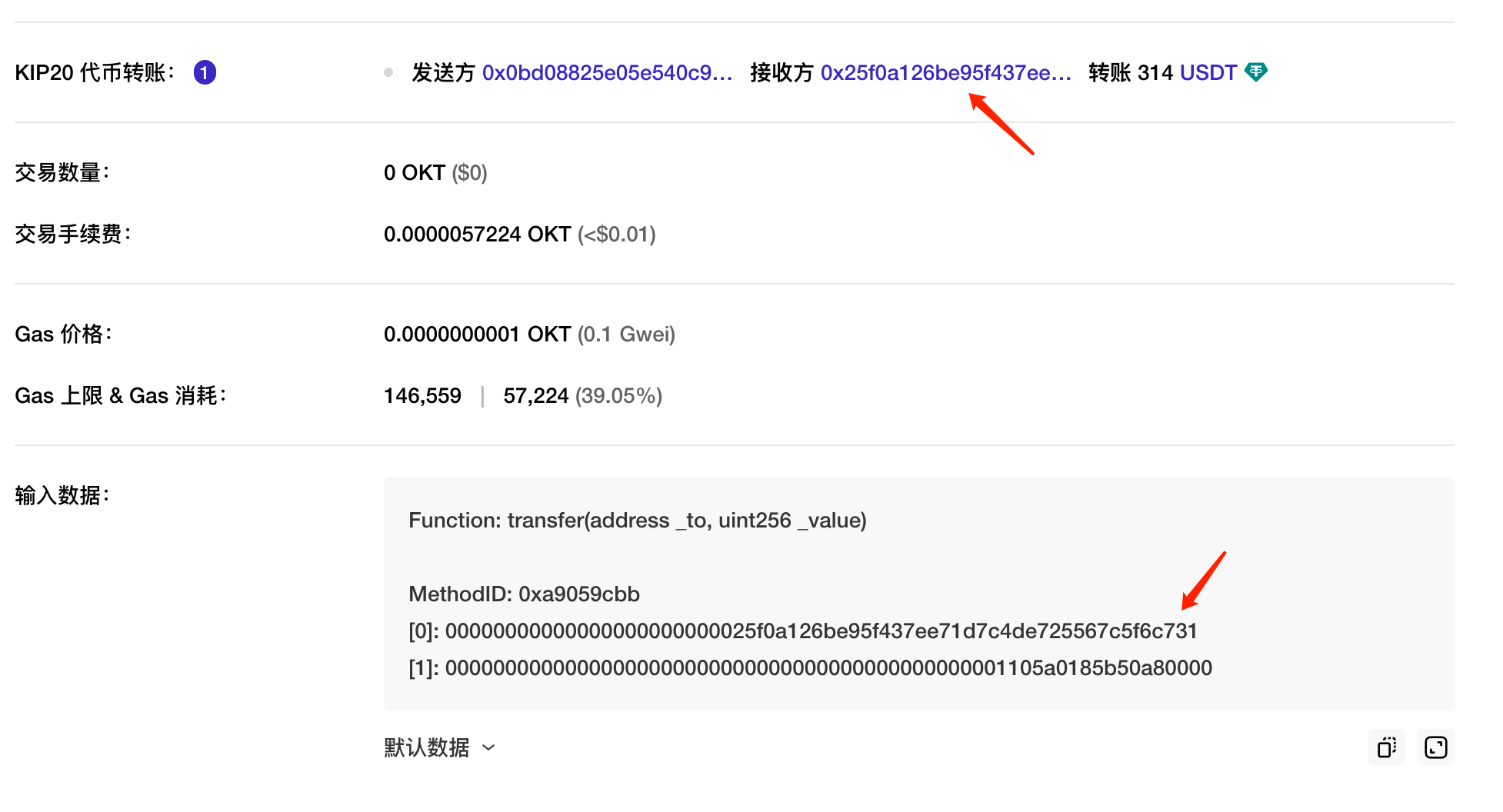
To prove that the address is mine, I used the recipient's address to transfer a bill to a black hole address.
The address of the black hole is:0x0000000000000000005757572e464d5a2e434f4d
The black hole address contains a post-decryption of the address:
~ % python -c 'print(bytes.fromhex("0000000000000000005757572e464d5a2e434f4d"))'
b'\x00\x00\x00\x00\x00\x00\x00\x00\x00WWW.FMZ.COM'
Afterword
I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm done here, I'm I'm pretty sure there are errors in the official chart, or at least I was lucky enough to decipher the answer before it was published, and I hope OKX is more rigorous the next time it hosts a similar event.
- Quantitative Practice of DEX Exchanges (2) -- Hyperliquid User Guide
- DEX exchange quantitative practices ((2) -- Hyperliquid user guide
- Quantitative Practice of DEX Exchanges (1) -- dYdX v4 User Guide
- Introduction to Lead-Lag Arbitrage in Cryptocurrency (3)
- DEX exchange quantitative practice ((1) -- dYdX v4 user guide
- Introduction to the Lead-Lag suite in digital currency (3)
- Introduction to Lead-Lag Arbitrage in Cryptocurrency (2)
- Introduction to the Lead-Lag suite in the digital currency (2)
- Discussion on External Signal Reception of FMZ Platform: A Complete Solution for Receiving Signals with Built-in Http Service in Strategy
- Discussing FMZ platform external signal reception: a complete set of strategies for the reception of signals from built-in HTTP services
- Introduction to Lead-Lag Arbitrage in Cryptocurrency (1)
- Application of the _Thread function in JavaScript policy design
- Teach you to design template class library to get K-line data of specified length
- Teaches you to design a template library for obtaining specified K-length line data
- Get Started with web3 Development Easily Based on Ethereum Using FMZ
- Explore the new functions of FMZ strategy editor: How ChatGPT improves your quantitative productivity significantly
- Explore the new features of the FMZ Strategy Editor: How ChatGPT dramatically improves your quantitative productivity
- Easy introduction to web3 development based on Ethereum with FMZ
- Digital Currency High-Frequency Strategy Detailed Introduction
- Introduction to Detailed High-Frequency Trading Strategies for Cryptocurrencies
- How to Solve the World Pi Day OKX Private Key Puzzle Award (with complete code)
- High frequency strategies for digital currencies
- Concurrent Strategy Execution with JavaScript Multithreading Support
- Make policy programs really run in parallel, adding multi-threaded support to JavaScript policies at the bottom of the system
- If you don't know how to write a strategy in such an easy-to-learn and easy-to-use Pine language...
- Expected gains from high-frequency trading
- Can we make quantitative trading without code? Let's find out...
- "Get the best deal" analysis of the vulnerability in the exchange
- 5.6 Build probability thinking to improve your trading pattern
- Elegant and simple! Accessed Uniswap V3 on FMZ with 200 lines of code
- When FMZ encounters ChatGPT, an attempt to use AI to assist in learning quantitative trading
DadyHow long does it take to do 1.04 million times?
JohnnyZ is a bully!
btcrobotThe ability to get things done.
Orc quantifiedZ is a bully!
Inventors quantifiedAbout 20 minutes.
Inventors quantifiedThe old iron is here.